Advanced Features
GraphQL security observability query depth admin secret rate limiting DoS protectionIn this document you can find information about the advanced GraphQL features available in some of our plans (see our pricing page for details).
Observability
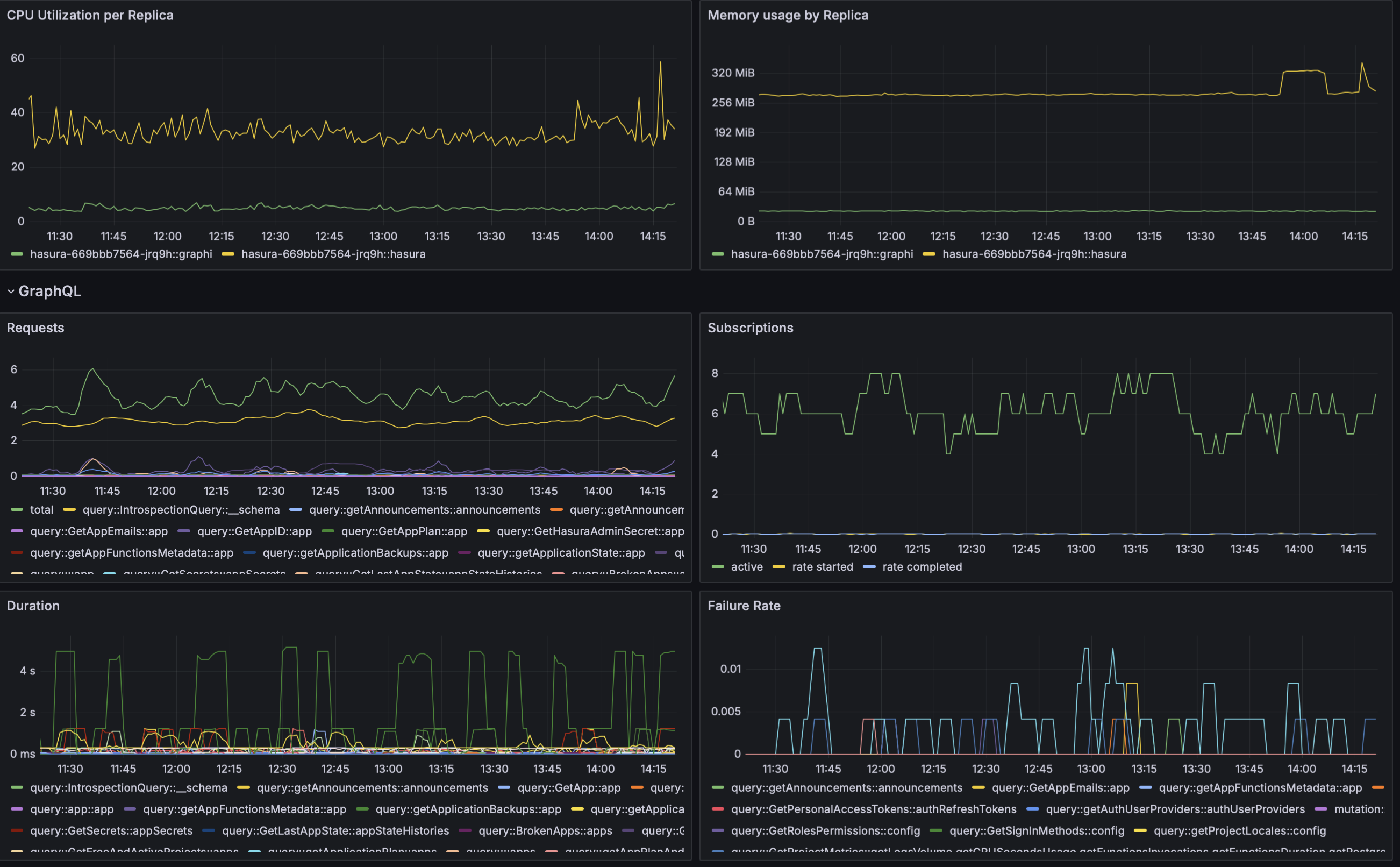
Section titled “Observability”In addition to resource utilization, as part of this set of advanced GraphQL features, you have extra visibility at the query level:
- CPU and Memory resources consumed by each replica (
hasura-graphiis the process responsible for these features) - Rate of requests
- Failure rate
- Requests duration
All of the added GraphQL metrics are broken down per:
- Operation (query/mutation)
- Name of the GraphQL request
- Types included in the request
For instance, below you can see a screenshot from our own staging application:
Security Features
Section titled “Security Features”In addition, a few security features are made available.
Forbid admin secret
Section titled “Forbid admin secret”This feature will block requests to any endpoint with the header x-hasura-admin-secret. To enable it:
[graphql.security]forbidAminSecret = trueMaximum Query Depth
Section titled “Maximum Query Depth”Deeply nested queries can require lots of resources which, in turn, may lead to resource exhaustion. It can also make your application susceptible to DoS attacks. To prevent this, you can configure the maximum query depth you want to allow. For instance, you can limit the depth of your queries to 4 with:
[graphql.security]maxDepthQueries = 4With the configuration above, the following query will be rejected:
query SomeNestedQuery { a { b { c { d { e } } } }}while:
query NotSoNestedQuery { a { b { c } }}will work just fine.
In addition to the logs you already have a new service will show in your “Logs” tab; hasura-graphi. Here you can see security events in the case you have enabled any of the security features mentioned above.