Rate Limits
rate limits API protection brute force prevention request throttling abuse prevention IP rate limitingRate limits in an HTTP API are essential for protecting services against abuse and brute force attacks by restricting the number of requests a client can make within a specified time period. By enforcing rate limits, we can mitigate the risk of unauthorized access, denial of service attacks, and excessive consumption of resources.
Limits work by setting a maximum number of requests (burst amount) allowed for a key within a specified time frame (recovery time). For example, with a limit of 30 requests and a recovery time of 5 minutes, a user can make up to 30 requests before hitting the limit. Additionally, the user receives an extra request every 10 seconds (5 * 60 / 30) until reaching the limit.
GraphQL/Storage/Functions
Section titled “GraphQL/Storage/Functions”You can rate-limit the GraphQL, Storage, and Functions services independently of each other. These rate limits are based on the client IP, and requests made to one service do not count toward the rate limits of another service.
Configuration
Section titled “Configuration”Project Dashboard -> Settings -> Rate Limiting
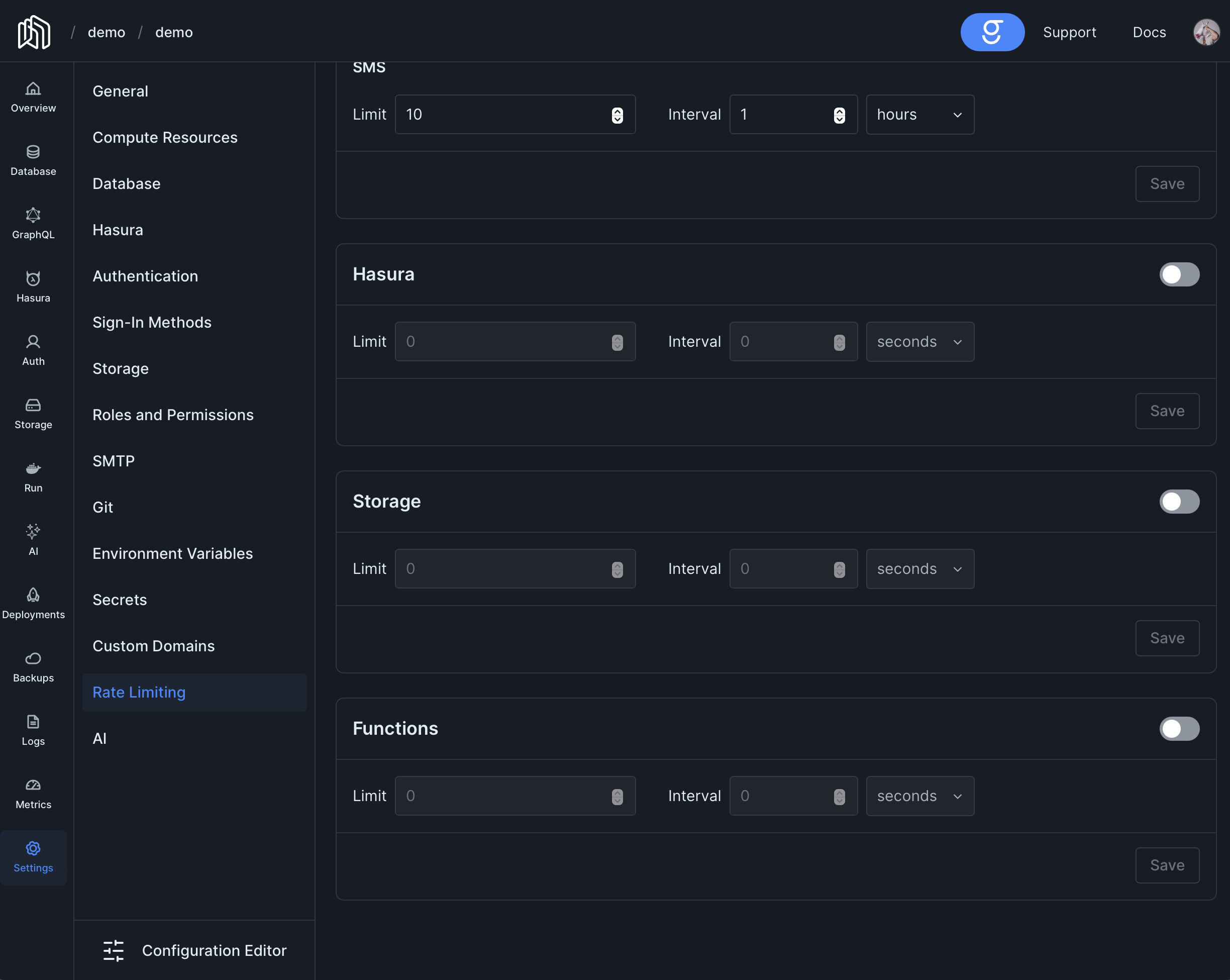
[hasura.rateLimit]limit = 100interval = '15m'
[functions.rateLimit]limit = 100interval = '15m'
[storage.rateLimit]limit = 100interval = '15m'Given that not all endpoints are equally sensitive, Auth supports more complex rate-limiting rules, allowing you to set different configurations depending on the properties of each endpoint.
| Endpoints | Key | Limits | Description | Minimum version |
|---|---|---|---|---|
| Any that sends emails1 | Global | 10 / hour | Not configurable. This limit applies to any project without custom SMTP settings | 0.33.0 |
| Any that sends emails1 | Client IP | 10 / hour | Configurable. This limit applies to any project with custom SMTP settings and is configurable | 0.33.0 |
| Any that sends SMS2 | Client IP | 10 / hour | Configurable. | 0.33.0 |
| Any endpoint that an attacker may try to brute-force. This includes sign-in, verify, and OAuth2 authorize/login endpoints3 | Client IP | 10 / 5 minutes | Configurable | 0.33.0 |
| Signup endpoints4 | Client IP | 10 / 5 minutes | Configurable | 0.33.0 |
| OAuth2 server-to-server endpoints5 | Client IP | 100 / 5 minutes | Configurable. Higher limit to accommodate backend services making requests on behalf of multiple users from a single IP | - |
| Any | Client IP | 100 / minute | The total sum of requests to any endpoint (including previous ones) can not exceed this limit | 0.33.0 |
1 Paths included:
/signin/passwordless/email/user/email/change/user/email/send-verification-email/user/password/reset/signup/email-password- If email verification enabled/user/deanonymize- If email verification enabled
2 Paths included:
/signin/passwordless/sms
3 Paths included:
/signin/**/verify*/otp/oauth2/authorize/oauth2/login
4 Paths included:
/signup/*/oauth2/register
5 Paths included:
/oauth2/token/oauth2/introspect
Configuration
Section titled “Configuration”Project Dashboard -> Settings -> Rate Limiting
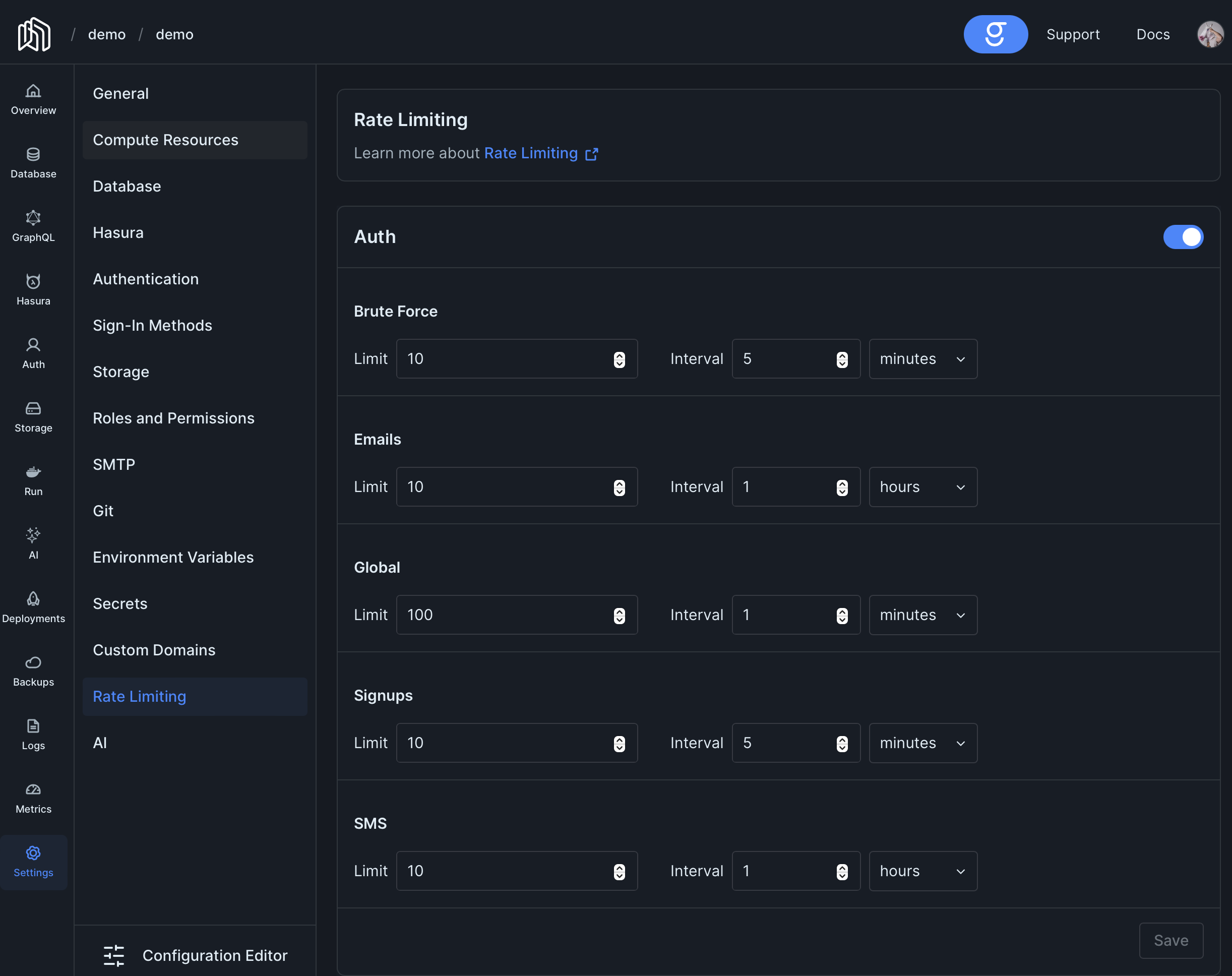
[auth.rateLimit][auth.rateLimit.emails]limit = 10interval = '1h'
[auth.rateLimit.sms]limit = 10interval = '1h'
[auth.rateLimit.bruteForce]limit = 10interval = '5m'
[auth.rateLimit.signups]limit = 10interval = '5m'
[auth.rateLimit.oauth2Server]limit = 100interval = '5m'
[auth.rateLimit.global]limit = 100interval = '1m'